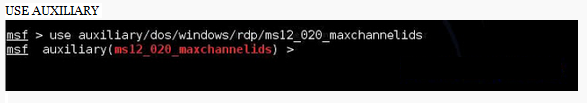
INTRODUCTION
- This module exploits the MS12-020 RDP vulnerability originally discovered and reported by Luigi Auriemma.
- The flaw can be found in the way the T.125 ConnectMCSPDU packet is handled in the maxChannelIDs field, which will result an invalid pointer being used, therefore causing a denial-of-service condition.
1.0 HOW TO
OPEN METASPLOIT FRAMEWORK
1.1 METASPLOIT
FRAMEWORK OPENED
1.2 SHOW
OPTIONS
- Use show options command to see the required fields.
- In this auxiliary you have set the RHOST .
- See the below image for more details -
1.3 SET
RHOST
- In my case victim ip address is : 192.168.72.131.
- See the below image for more details .
1.4 RUN
- As you type the run and press enter .
- It sends the crafter packets of 210 bytes through the port 3389.
- This sending of packet will the crash the windows xp system and xp system will restarted .
- Then in the below image you will see it check for the RDP status and it shows that " it seems down ".
- See the below image for more help -
1.5 VICTIM
SYSTEM RESTARTED
- So this will happen , my system is restart again after crashed.
1.6 CONCLUSION
- All xp users this is a bad news for you anyone can crash your system if you don't have prevention measures.
- Try to install patches .
- BACK TRACK USER : Good for practise . Use it , learn it , Remember this vulnerability in future also may be you will somewhere else .


















.png)



0 comments:
Post a Comment